Category: Linux
Debian 9.5 join in Windows Active Directory Domain

If you want to make Windows users access the Linux server, you must establish a connection to the Active Directory domain. The configuration will be made from the point of view of Linux Administrator. Configuring Windows Server leave for Windows administrators. The General scheme of connection operation is shown in the figure below.
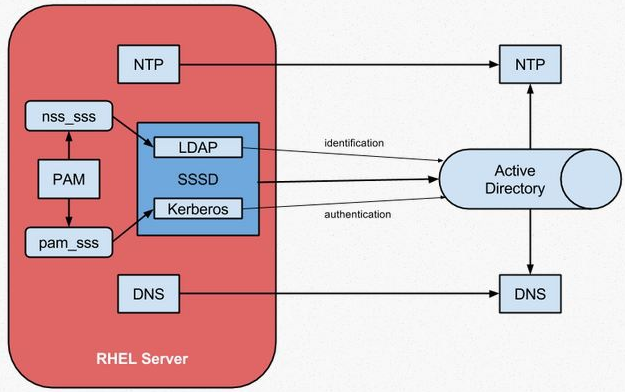
You can use Winbind for authorization, but It requires the installation of a Samba server. In order to avoid this instead of Winbind, I used the SSSD service.
1. Install packages:
apt-get -y install ntp realmd adcli krb5-user packagekit sssd sssd-tools samba-common samba-common-bin samba-libs2. Edit hostname
vim /etc/hostnameAdd to file:
debian-ad3. Edit hosts file:
vim /etc/hostsAdd line:
127.0.1.1 debian-ad.domain.local debian-ad4. Add your DNS servers that are installed on domain controllers.
vim /etc/resolv.confAdd to file:
domain domain.local
nameserver ip_address_domain1
nameserver ip_address_domain25. To communicate with Active Directory, the time must be identical on all servers. Edit /etc/ntp.conf
vim /etc/ntp.confserver ip_address_domain1
server ip_address_domain2Verify:
ntpq -p6. Edit the Kerberos configuration file:
vim /etc/krb5.confAdd to file:
[libdefaults]
default_realm = DOMAIN.LOCAL
...
[realms]
HYPERDEV.LOCAL = {
kdc = DOMAIN.LOVAL
admin_server = DOMAIN.LOCAL
default_domain = DOMAIN.LOCAL
}
...
[domain_realm]
.domain.local = DOMAIN.LOCAL
domain.local = DOMAIN.LOCAL
...
7. The first time a new user is authorized, a directory will be created in the /home directory. To do this, edit the pam configuration file and add the appropriate module to it:
vim /etc/pam.d/common-sessionAdd to file:
session optional pam_mkhomedir.so skel=/etc/skel umask=0778. Domain discovery:
realm discover DOMAIN.LOCAL9. Connect to the domain using the domain controller administrator login and password:
realm join -U admin_login domain.local10. In order not to use the domain name when connecting and identifying the user, you must change the string in the SSSD configuration file:
vim /etc/sssd/sssd.confIn the file, change the True parameter to False:
use_fully_qualified_names = False11. To clear the cache, add a command to crontab that will be executed every minute:
crontab -eAdd to file:
* * * * * /usr/sbin/sss_cache -E12. Restart sssd service:
/etc/init.d/sssd restart13. Check the domain connection:
adcli info DOMAIN.LOCAL14. Verify the active directory user:
root@debian-adt:~# id testuser
uid=1410202124(testuser) gid=1410200513(domain users) groups=1410200513(domain users)
Posted: 2018-10-28

2018-10-29 12:15:17
emkill
good